The 'Expected result' in each test page apply to the default settings of CanvasBlocker if not stated otherwise. If you get different results and do not understand why. Description This extension protects user privacy by prevents the HTML canvas element from being used by malicious scripts for fingerprinting the user. This extension adds a slight noise to the data generated by the canvas element when certain methods are being called. This way the canvas element cannot be used for fingerprinting purposes. CanvasBlocker; uMatrix(停止維護了; 0x0d 如何切換到Firefox. 不可否認,Chrome能夠混到今天這個市場份額,必定有它很優秀的地方,crx的兼容性確實很不錯,不然為什麼那麼多瀏覽器直接抄或者是採用Chromium內核開發? 只要幾分鐘,即可從 Chrome 切換到 Firefox. Thought your canvas fingerprint blocker made you incognito? As many know, canvas fingerprinting is the most recent development in web tracking. In the past, the easiest way to prevent web tracking was to block out the method of tracking entirely. For example, to prevent cookie tracking, you simply disable cookies in your browser. HI, I'm using CanvasBlocker and I'm starting to ask myself whether it's still necessary/useful to protect our privacy, considering that. Latest Firefox versions have built-in Fingerprints protection.
These are our current web browser recommendations and some tweaks you can use to preserve your privacy.
Firefox is fast, reliable, open-source, and respects your privacy. Don't forget to adjust the settings according to our recommendations: Privacy Add-ons WebRTC about:config tweaks.
Tor Browser is your choice if you need an extra layer of anonymity. It's a modified version of Firefox ESR, which comes with pre-installed privacy add-ons, encryption, and an advanced proxy. How does Tor work?
Firefox is fast, reliable, open-source, and respects your privacy. Don't forget to adjust the settings according to our recommendations: Privacy Add-ons WebRTC about:config tweaks.
Tor Browser is your choice if you need an extra layer of anonymity. It's a modified version of Firefox ESR, which comes with pre-installed privacy add-ons, encryption and an advanced proxy. How does Tor work?
Bromite is a Chromium-based browser with privacy and security enhancements, built-in adblocking and DNS over HTTPS support; it includes patches from ungoogled-chromium and other privacy-focused projects. More info can be found on the official website.
Worth Mentioning for Android
- Privacy Browser - An open-source web browser focused on user privacy. Features include integrated ad blocking with EasyList, SSL certificate pinning, and Tor Orbot proxy support. Keep WebView up-to-date
Firefox is fast, reliable, open-source, and respects your privacy. Note: Because of limitations set by Apple in iOS, our recommended tweaks cannot be applied. However, Firefox for iOS has an Enhanced Tracking Protection feature that uses a list provided by Disconnect to identify and block ad, social, and analytics trackers, as well as cryptominers and fingerprinters.
Onion Browser is an open-source browser that lets you browse the web anonymously over the Tor network on iOS devices and is endorsed by the Tor Project. Warning: there are certain anonymity-related issues with Onion Browser due to iOS limitations.
DuckDuckGo Privacy Browser is an open-source web browser that has built-in ad and tracker blocking and utilizes ToS;DR to rate the privacy policies of the sites you visit.
Worth Mentioning for iOS
- SnowHaze - An open-source web browser with built-in ad, tracker, cookie, and fingerprint blocking, all customizable on a per-site basis.
When you visit a web page, your browser voluntarily sends information about its configuration, such as available fonts, browser type, and add-ons. If this combination of information is unique, it may be possible to identify and track you without using cookies. EFF created a Tool called Panopticlick to test your browser to see how unique it is.
You need to find what most browsers are reporting, and then use those variables to bring your browser in the same population. This means having the same fonts, plugins, and extensions installed as the large installed base. You should have a spoofed user-agent string to match what the large userbase has. You need to have the same settings enabled and disabled, such as DNT and WebGL. You need your browser to look as common as everyone else. Disabling JavaScript, using Linux, or even using the Tor Browser Bundle, will make your browser stick out from the masses.
Modern web browsers have not been architected to assure personal web privacy. Rather than worrying about being fingerprinted, it seems more practical to use free software plugins to regain control. They not only respect your freedom, but your privacy also. You can get much further with these than trying to manipulate your browser's fingerprint.
Related Information
- BrowserLeaks.com - Web browser security testing tools that tell you what exactly personal identity data may be leaked without any permissions when you surf the Internet.
While software like NoScript prevents this, it's probably a good idea to block this protocol directly as well, just to be safe. Note: This disables browser-based call functionality that is used for webapps like Discord, Hangouts, Jitsi, etc.
How to disable WebRTC in Firefox?
In short: Set 'media.peerconnection.enabled' to 'false' in 'about:config'.
Explained:
- Enter 'about:config' in the firefox address bar and press enter.
- Press the button 'I'll be careful, I promise!'
- Search for 'media.peerconnection.enabled'
- Double click the entry, the column 'Value' should now be 'false'
- Done. Do the WebRTC leak test again.
If you want to make sure every single WebRTC-related setting is really disabled change these settings:
- media.peerconnection.turn.disable = true
- media.peerconnection.use_document_iceservers = false
- media.peerconnection.video.enabled = false
- media.peerconnection.identity.timeout = 1
Now you can be 100% sure WebRTC is disabled.
How to disable WebRTC in Safari?
Safari is far stricter with WebRTC than other major browsers, and it does not leak your IP address in its default configuration. If you'd like, you can follow these steps just to double-check your browser:
- Choose 'Preferences' under the Safari menu in your menu bar.
- Select the Advanced tab and check the 'Show Develop menu in menu bar' box.
- Exit Preferences and open the Develop menu in your menu bar.
- In the drop-down menu, open the 'WebRTC' submenu and ensure 'Enable Legacy WebRTC API' is unchecked. If it's grayed out, even better.
How to disable WebRTC in Google Chrome?
WebRTC cannot be fully disabled in Chrome; however, it is possible to change its routing settings (and prevent leaks) using an extension. Two open-source solutions include WebRTC Leak Prevent (options may need to be changed depending on the scenario), and uBlock Origin (select 'Prevent WebRTC from leaking local IP addresses' in Settings).
What about other browsers?
Chrome on macOS and Internet Explorer do not implement WebRTC yet. But we recommend using Firefox on all devices.
uBlock Origin is an efficient wide-spectrum blocker that is easy on memory, and yet can load and enforce thousands more filters than other popular blockers out there. It has no monetization strategy and is completely open source. Advanced mode allows for dynamic filtering. Dynamic filtering allows for extended blocking similar to NoScript and uMatrix (E.g. medium or hard) blocking.
HTTPS Everywhere enables encryption of your connections to many major websites, making your browsing more secure. It is a collaboration between The Tor Project and the Electronic Frontier Foundation.
Decentraleyes emulates Content Delivery Networks locally by intercepting requests, finding the required resource, and injecting it into the environment. This all happens instantaneously, automatically, and no prior configuration is required.
ClearURLs will automatically remove tracking elements from URLs to help protect your privacy when browsing through the Internet.
xBrowserSync synchronizes bookmarks across devices and browsers with end-to-end encryption. Data is encrypted and decrypted on the device, no one but you can read it. No registration is needed, just enter a randomly generated id or QR code on all devices. Different servers are available, and it can also be self-hosted.
Worth Mentioning
- floccus - Synchronize bookmarks across browsers via Nextcloud, WebDAV or a local file (and thus any file sync solution). For Firefox, Chrome, Edge.
Additional Functionality

Terms of Service; Didn’t Read is an addon that believes 'I have read and agree to the Terms of Service' is the biggest lie on the web, and wants to fix it by grading websites based on their terms of service agreements and privacy policies. It also gives short summaries of those agreements. The analysis and ratings are published transparently by a community of reviewers.
Snowflake is a new pluggable transport from the Tor Project. If you have an uncensored connection, running this extension volunteers your connection to be used as a Snowflake proxy to help users unable to connect to the Tor network. Your IP will not be visible to the sites users visit using your proxy, as this extension will not make you an exit node. If your access to the Tor network is blocked, this extension will not assist you, and you should use the Tor Browser instead. Note: This add-on does not work with WebRTC disabled.
Persistent storage management
Desktop
Temporary Containers allow you to open tabs, websites, and links in automatically managed disposable containers. Containers isolate data websites store (cookies, storage, and more) from each other, enhancing your privacy and security while you browse: Enhance your privacy in Firefox with Temporary Containers.
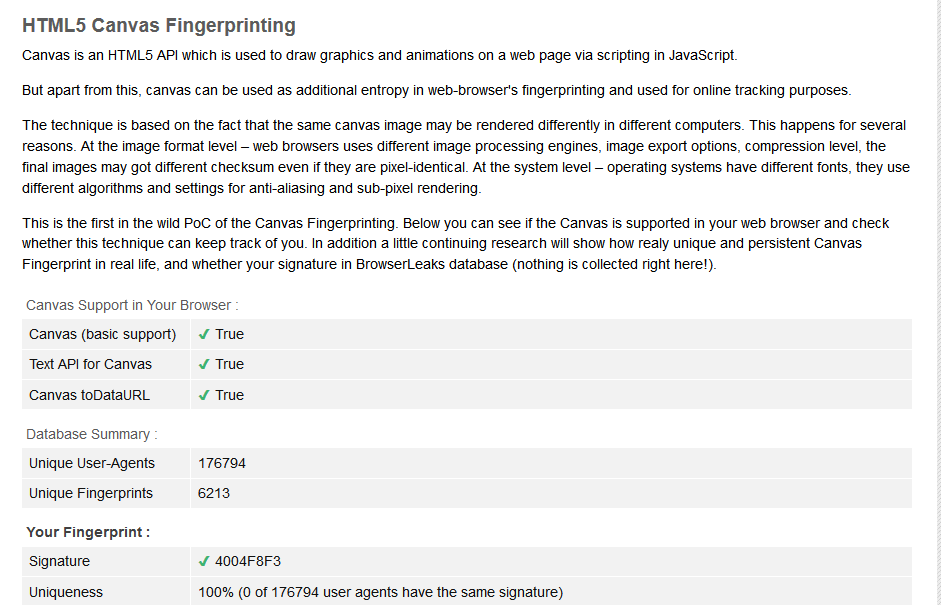
Canvasblocker Github
Firefox Multi-Account Containers allow you to create containers for specific websites. These containers are isolated from eachother. This add-on can be used in conjunctiuon with Temporary Containers to allow persistent logins to websites you specify.
Android
ETag Stoppa Prevents Firefox from storing entity tags by removing ETag response headers unconditionally and without exceptions.
Cookie AutoDelete automatically removes cookies, lingering sessions, and other information that can be used to spy on you when they are no longer used by open browser tabs.
For Advanced Users
uMatrix gives you control over the requests that websites make to other websites. Many websites integrate features which let other websites track you, such as Facebook Like Buttons or Google Analytics. uMatrix allows 1st party scripts in its default configuration. If you want the default functionality of NoScript consider blocking 1st party scripts everywhere by default. This addon has been discontinued.
CanvasBlocker allows users to prevent websites from using some Javascript APIs to fingerprint them. Users can choose to block the APIs entirely on some or all websites (which may break some websites) or just block or fake its fingerprinting-friendly readout API.
Preparation:
- Enter 'about:config' in the firefox address bar and press enter.
- Press the button 'Accept the Risk and Continue' [FF71+] or 'I accept the risk'.
- Copy and paste each of the preferences below (for example 'webgl.disabled') into the search bar, and set each of them to the stated value (such as 'true').
Getting started:
Disables playback of DRM-controlled HTML5 content, which, if enabled, automatically downloads the Widevine Content Decryption Module provided by Google Inc. Details
DRM-controlled content that requires the Adobe Flash or Microsoft Silverlight NPAPI plugins will still play, if installed and enabled in Firefox.
- 0 = Accept all cookies by default
- 1 = Only accept from the originating site (block third-party cookies)
- 2 = Block all cookies by default
Referer header when the full hostnames match. (Note: if you notice significant breakage, you might try 1 combined with an XOriginTrimmingPolicy tweak below.) Source- 0 = Send
Refererin all cases - 1 = Send
Refererto same eTLD sites - 2 = Send
Refereronly when the full hostnames match
Referer across origins, only send scheme, host, and port in the
across origins, only send scheme, host, and port in the Referer header of cross-origin requests. Source- 0 = Send full url in
Referer - 1 = Send url without query string in
Referer - 2 = Only send scheme, host, and port in
Referer
- 0 = Store extra session data for any site. (Default starting with Firefox 4.)
- 1 = Store extra session data for unencrypted (non-HTTPS) sites only. (Default before Firefox 4.)
- 2 = Never store extra session data.
- network.dns.disablePrefetch = true
- network.dns.disablePrefetchFromHTTPS = true
- network.predictor.enabled = false
- network.predictor.enable-prefetch = false
- network.prefetch-next = false
Canvasblocker Settings
Firefox Offscreencanvas
Firefox user.js Templates
- arkenfox user.js (formerly ghacks-user.js) - An ongoing comprehensive user.js template for configuring and hardening Firefox privacy, security and anti-fingerprinting.
Related Information
Canvasblocker Safari
- Firefox Privacy: Tips and Tricks for Better Browsing - A good starting guide for users looking to keep their data private and secure.
- ffprofile.com - Helps you to create a Firefox profile with the defaults you like.
- Privacy Settings - A Firefox add-on to alter built-in privacy settings easily with a toolbar panel.
- Firefox Privacy Guide For Dummies - Guide on ways (already discussed and others) to improve your privacy and safety on Firefox.
